- New incident Cases can easily be added; plus, various Case details can be created, including names, description, serial numbers and in-charge investigators.
- While creating a Case, you can choose whether to automatically perform OCR and the languages to be converted to.
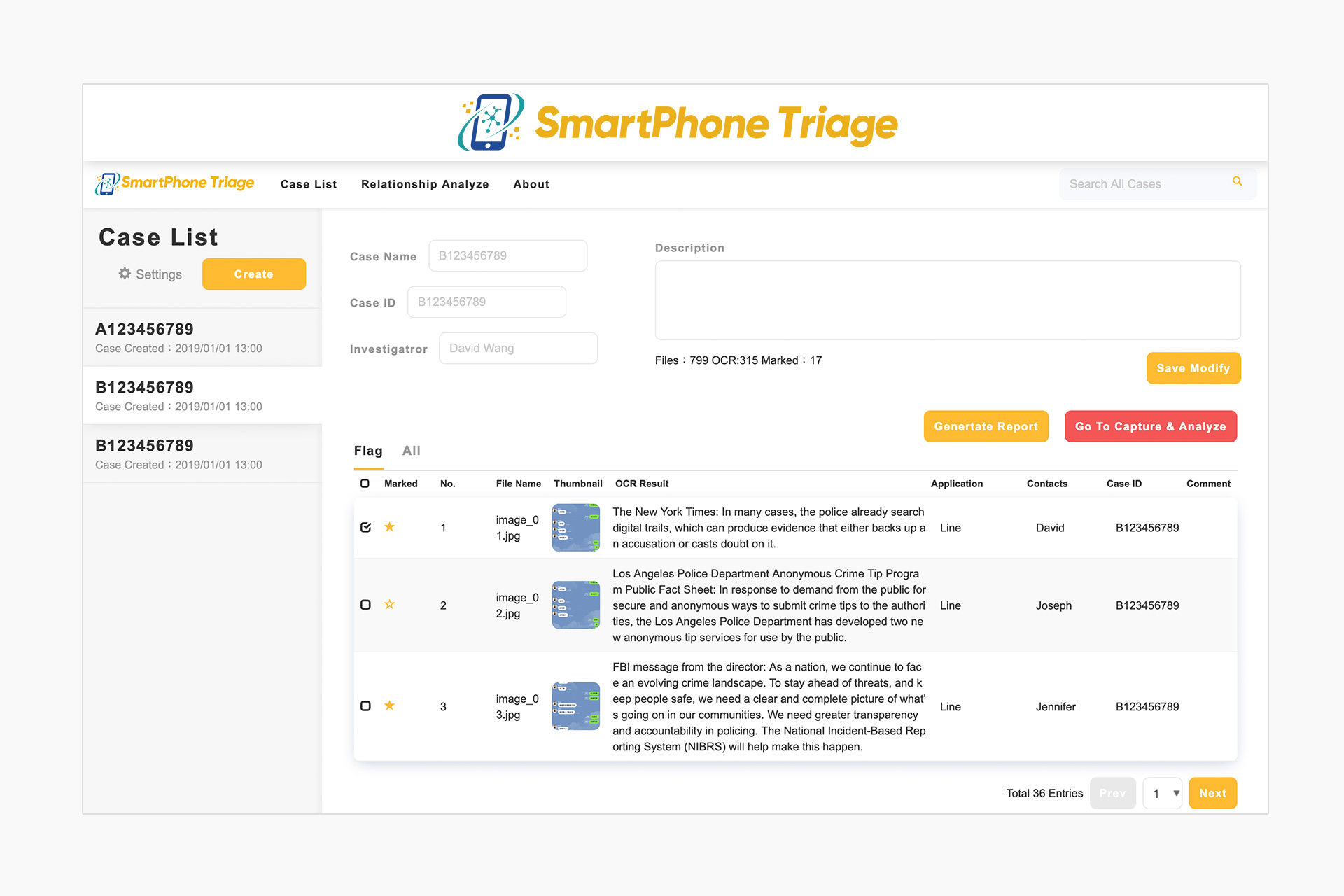
- Can select the current Case to display all case information, including name, serial number, in-charge investigator and abstract, all of which can easily be modified and saved.
- Using device connection detection, it can detect whether or not the Android/iOS phone under investigation is currently connected.
- For Android devices with USB Debugging enabled, it offers different screenshot modes including “Automatic”, “Batch Automatic”, “Single”, “Semi-Automatic”, “Continuous” and “File Import”.
- Upon connecting to iOS device's interface, it supports single/multiple screenshot(s) via automatic/manual scrolling. The automatic scrolling feature should be performed when the voice control of the device is turned
on.
- Through the built-in Airplay function of iOS devices, it offers different screenshot modes including “Single”, “Scheduled”, “Semi-Automatic”, “Recording” and “File Import”.
- The “File Import” function offers the analysis of videos in H264 format.
- Through the Character Recognition(OCR) function, the image file's text content is identified and saved to the database, allowing for future searches.
- Using the keyword Search function, the search scope can span a single Case or many Cases.
- Resulting information displayed include: annotation, serial number, thumbnail, OCR result, application, contact, and case number. All the above information can further be filtered and sorted.
- Can click the thumbnails to view the screenshots as well as related information, and translate the OCR results into different languages.
- Multiple screenshots can be selected to be included in the report.
- The report's front and back covers can be customized on the Settings page.
- The generated report may include items such as: image, file names, date of capture, and file's digital fingerprint.
- Report output formats support English/Mandarin.
- Also provided, is a feature used to upload the report's hash value to blockchain for permanent evidence preservation.
- In Analysis Mode, can select the date range and check the OCR results in a chat view. LINE, Hangouts, Telegram, Skype, Whatsapp are supported in the Analysis mode.
- Can select the cases, applications and contacts to conduct cross-case Relationship Analysis and choose whether to merge the contacts with same names.
- Can click the connecting lines in the Relationship Graphic to view the contents of threads.
- Can tick the types of files to display the records of file transfer in the chat threads.
|